Data Security Microservice Application
Septian Geges
Summary
Purpose of the Application
This application is a data security microservice designed to securely encrypt and decrypt data. Developed using Node.js, Express and custom algorithms, the application allows users to secure their data through a simple web interface.
Description
Data Security Microservice Application with Node.js
Purpose of the Application
This application is a data security microservice designed to securely encrypt and decrypt data. Developed using Node.js, Express and custom algorithms, the application allows users to secure their data through a simple web interface.
Key Features
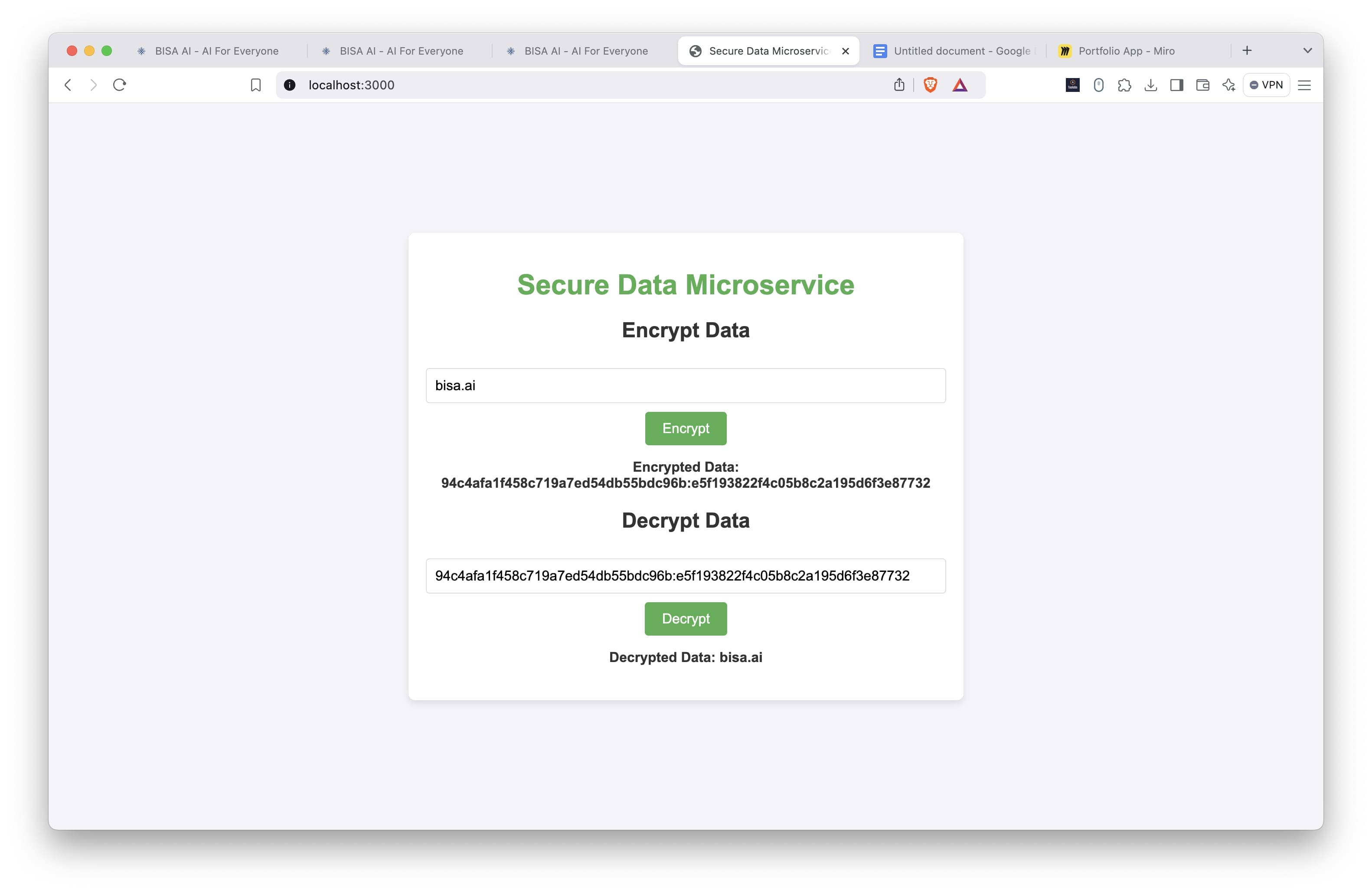
- Data Encryption:
- Users can input plaintext data through the web interface.
- Data is encrypted using the AES-256-CBC algorithm, which is renowned for its security and reliability in symmetric encryption.
- The encrypted result is displayed on the screen for users to view and copy.
- Data Decryption:
- Users can input encrypted data that they wish to return to its original form.
- The application decrypts the data using the same encryption key, restoring it to readable plaintext.
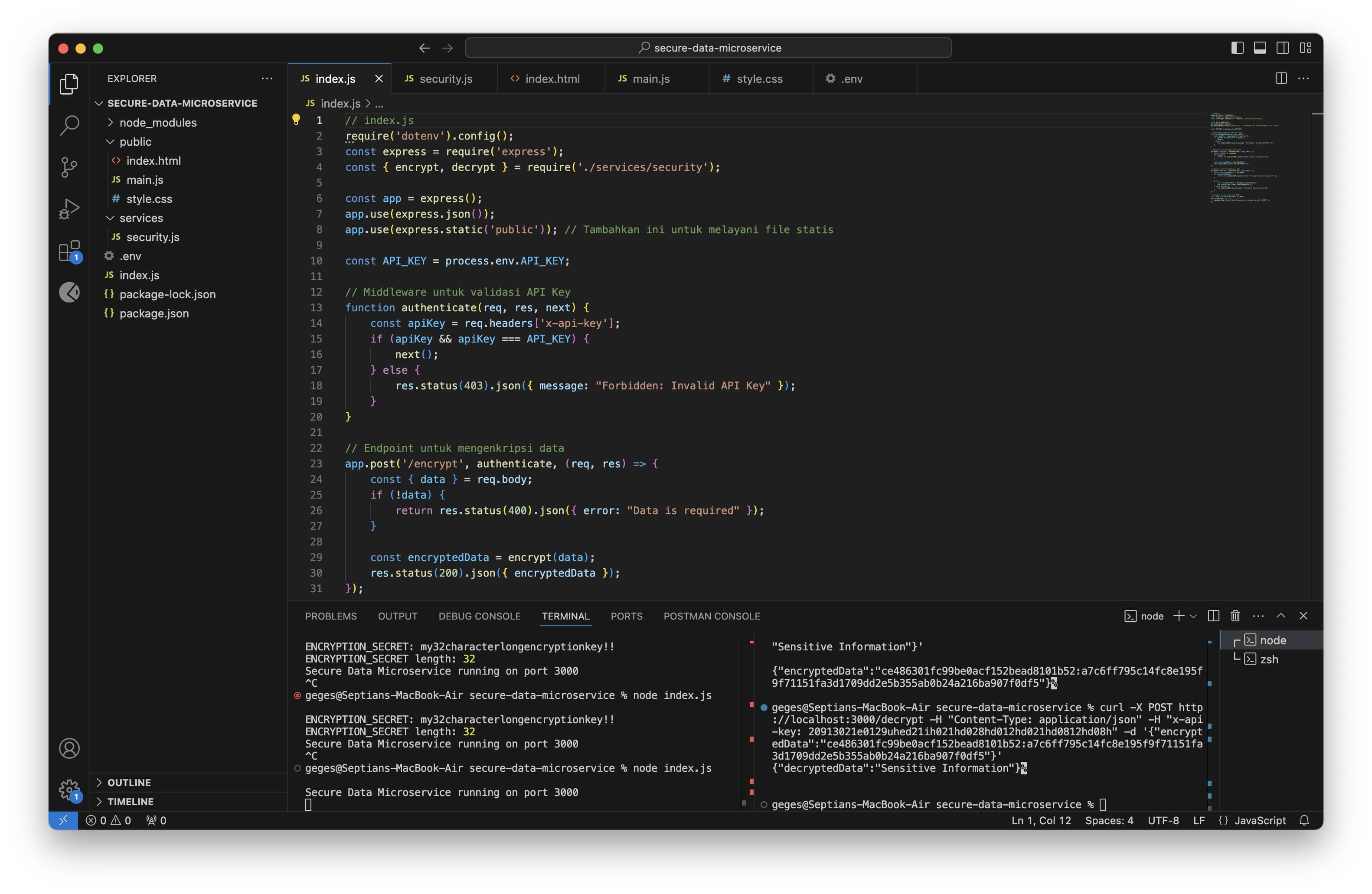
- API Key Authentication:
- The application is equipped with authentication middleware to validate the API Key before users can utilize the encryption/decryption functions.
- This feature ensures that only authorized users can access the encryption/decryption services.
Changes Made:
- Unique Key Generation:
- A new function generateUniqueKey is added, which creates a unique key based on the original ENCRYPTION_SECRET. This is done by hashing the secret with SHA-256 and taking the first 32 bytes (256 bits), which is suitable for AES-256.
- Key Usage:
- Both the encrypt and decrypt functions now utilize the unique key generated from ENCRYPTION_SECRET.
Advantages:
- Increased Security: By deriving a unique key from your original secret, you ensure that even if someone knows your ENCRYPTION_SECRET, they cannot directly use it without the hash transformation.
- Consistency: The same transformation will produce the same key for the same secret, ensuring that encryption and decryption remain consistent.
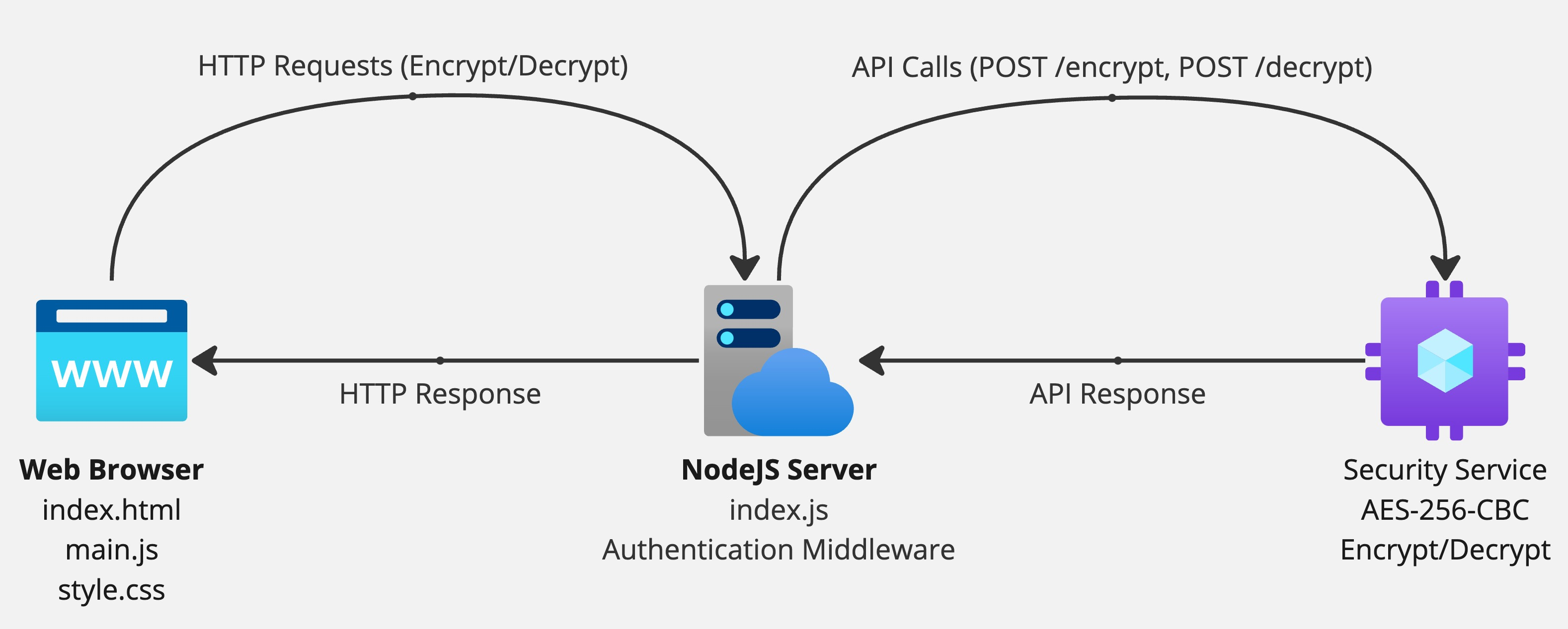
Folder Structure and Components
- index.js:
- The main file that initializes the Express server and defines the /encrypt and /decrypt endpoints.
- Manages authentication through middleware that checks the API Key.
- Utilizes functions from services/security.js to handle the encryption/decryption logic.
- services/security.js:
- Contains the core logic for encrypting and decrypting data.
- Utilizes the built-in crypto module from Node.js to implement the AES-256-CBC algorithm.
- public/:
- index.html: The HTML file providing the user interface for entering data to be encrypted or decrypted.
- main.js: JavaScript script that sends encryption and decryption requests from the user interface to the server using the Fetch API.
- style.css: CSS file that enhances the user interface, making it more modern and user-friendly.
Application Workflow
- Users access the main page at http://localhost:3000.
- To encrypt data, users enter plaintext in the input field under the “Encrypt Data” section and click the "Encrypt" button.
- The data is sent to the server via a POST request to the /encrypt endpoint, along with the API Key in the header.
- The server returns the encrypted result, which is then displayed on the screen.
- To decrypt data, users enter the encrypted data in the “Decrypt Data” section and click the "Decrypt" button.
- The data is sent to the server via a POST request to the /decrypt endpoint.
- The server returns the decrypted result, which is displayed on the screen.
Technologies Used
- Node.js: JavaScript runtime for running the application server.
- Express: A minimalist framework for Node.js that simplifies API and route creation.
- Crypto Module: A built-in Node.js module for handling data encryption using the AES-256-CBC algorithm.
- HTML, CSS, and JavaScript: The user interface is built using HTML for structure, CSS for styling, and JavaScript for dynamic interaction with the server.
Usage Steps
Install Dependencies: Ensure all dependencies are installed using the command:
bash
npm install
Configure Environment: Create a .env file to define the API_KEY and ENCRYPTION_SECRET used in the encryption and decryption processes.
Run the Server: Start the server with the command:
bash
node index.js
Access the Interface: Open http://localhost:3000 in a browser and start encrypting/decrypting data.
Informasi Course Terkait
Kategori: Cyber SecurityCourse: Persiapan Sertifikasi Internasional CyberSAFE (Cyber Security Awareness For Everyone)