Simulation of Block Cipher Operation Between 2 VPS
Novi Trisman Hadi
Summary
Block Cipher Operation Modes are techniques used in cryptography to encrypt or decrypt data in fixed blocks using block cipher algorithms such as AES (Advanced Encryption Standard). Block ciphers operate on data blocks of a specific size, such as 128 bits. In this simulation, VPS 1 will send a secret message to VPS 2. Before sending the message, it will be encrypted using the Block Cipher Operation Mode ECB. Once successfully sent, VPS 2 will decrypt the file, allowing the message to be opened by VPS 2.
Description
Summary
Block Cipher Operation Modes are techniques used in cryptography to encrypt or decrypt data in fixed blocks using block cipher algorithms, such as AES (Advanced Encryption Standard). Block ciphers operate on data blocks of a specific size, such as 128 bits. In this simulation, VPS 1 will send a secret message to VPS 2. Before sending, the message will be encrypted using the Block Cipher Operation Mode ECB. Once successfully sent, VPS 2 will decrypt the file, allowing the message to be opened by VPS 2.
Description
Block Cipher Operation Modes are techniques used in cryptography to encrypt or decrypt data in fixed blocks using block cipher algorithms, such as AES (Advanced Encryption Standard). Block ciphers operate on data blocks of a specific size, such as 128 bits.
Block cipher operation modes allow the use of block ciphers to encrypt or decrypt data in sizes larger than one block. This is necessary because block ciphers fundamentally operate on one data block at a time.
Some commonly used block cipher operation modes include:
1. ECB (Electronic Codebook): This mode encrypts each data block separately and independently. This results in identical blocks in the plaintext producing identical blocks in the ciphertext. ECB mode does not provide additional security for data with the same patterns.
2. CBC (Cipher Block Chaining): This mode combines the plaintext block with the previous ciphertext block before encryption. Each ciphertext block is generated by XORing the plaintext block with the previous ciphertext block. CBC requires an initialization vector (IV) as the initial input for the first block. CBC mode is more secure than ECB because it does not produce the same patterns for the same ciphertext blocks of different plaintext blocks.
3. CTR (Counter): This mode transforms the block cipher into a pseudorandom number generator using a counter. Each plaintext block is encrypted using a changing counter, and the resulting encryption is XORed with the plaintext block to produce the ciphertext block. CTR mode allows for parallel encryption and decryption, making it more efficient.
4. OFB (Output Feedback): This mode transforms the block cipher into a keystream generator. The generated keystream is used to perform XOR operations with the plaintext to produce the ciphertext. OFB mode can also work in a similar manner to CTR mode.
Simulation
- Login to VPS 1
- Make root folder
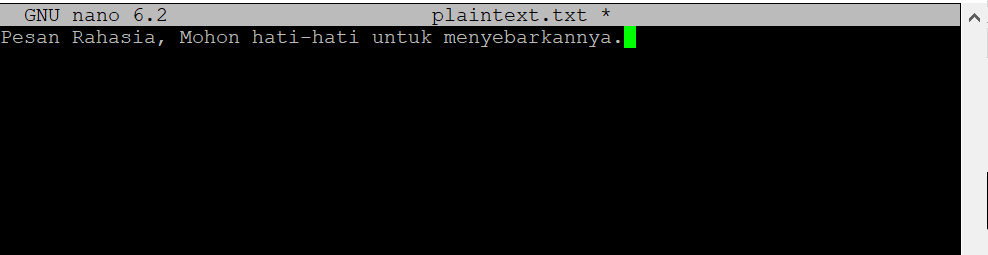
- Prepare a dataset of random text to be used as plaintext. For example, create a file named "plaintext.txt" and fill it with random text.
4. Fill the file "plaintext.txt", save, and exit.
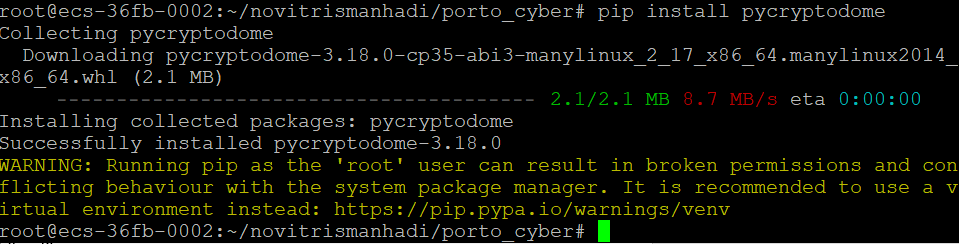
5. Install modul pycryptodome
6. Make encrypt.py file and write code bellow
7. Run the file encrypt.py. The program will read plaintext.txt, encrypt the text blocks using the corresponding key, and save the encryption results to the file ciphertext.txt. Execute the script or program on the first VPS to perform encryption.
8. Copy the file ciphertext.txt from the first VPS to VPS 2. You can use commands like scp or use a secure file transfer protocol such as SFTP.
Format Copy file iphertext.txt to VPS 2 :
9. Input password access root VPS 2
10. If the data copying is successful, a notification will appear as shown below.
11. Login to VM 2
12. Ceck root Folder
13. Install pycryptodome
14. Make file decrypt.py
15.Type the following code into the decrypt.py file. The program will read ciphertext.txt, decrypt the ciphertext blocks using the corresponding key, and save the decryption results to the decrypted.txt file.
16. Run the decrypt.py file. Execute the script or program on the second VPS to perform decryption.
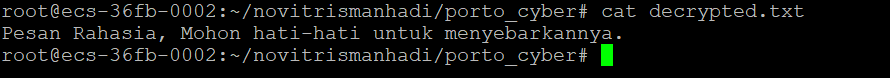
17. If successful, the decrypted.txt file will be generated.
18. Read the contents of the decrypted.txt file. Compare it with the contents of the plaintext.txt file. If they are the same, then the information security process using Block Cipher Operation Modes has been successful.
By following the steps above, you can simulate Block Cipher Operation Modes using two VPS and a dataset of random text. The chosen mode of operation is ECB, which is applied to both encryption and decryption processes on VPS 1 and VPS 2. The decryption results will be available in the decrypted.txt file on VPS 1 after the transfer is completed. Make sure to use the appropriate implementation of the block cipher algorithm with the chosen mode of operation and secure the data transfer process between the two VPS instances.
Informasi Course Terkait
Kategori: Cyber SecurityCourse: Persiapan Sertifikasi Internasional CyberSAFE (Cyber Security Awareness For Everyone)