Data delivery between servers using RSYNC encrypt
I Wayan Rangga Pinastawa
Summary
Data delivery between servers using RSYNC with encryption security is a method used to ensure the security and integrity of data transmitted between two servers. RSYNC is a protocol commonly used to transmit and synchronize files between different servers.
In data delivery using RSYNC, encryption security is used to protect data from potential threats such as theft or interception. Encryption is the process of converting data into a form that cannot be read without the correct encryption key. By using encryption, even if the transmitted data falls into the wrong hands, it will not be easy to read.
The data delivery between servers using RSYNC with encryption security involves several steps. First, the data to be transmitted is encrypted using a strong encryption algorithm. This can include the use of algorithms such as AES (Advanced Encryption Standard) or RSA (Rivest-Shamir-Adleman).
After the data is encrypted, it is transmitted through a secure connection between the two servers. A secure connection can be achieved by using protocols such as Secure Shell (SSH) or Virtual Private Network (VPN). These protocols provide an additional layer of security by using techniques such as authentication and additional encryption.
When the data reaches the destination server, it is decrypted using the appropriate encryption key. The encryption key is known only to those who have the proper access rights. This ensures that only authorized recipients can read and access the transmitted data.
By using data delivery between servers using RSYNC with encryption security, data security can be maintained during the delivery process. Threats such as theft or interception can be reduced, and data integrity can be ensured. It is important to choose a strong encryption algorithm and use secure connection protocols to protect the data transmitted between servers.
Description
Data delivery between servers using RSYNC with encryption security
First, we create a bash script to perform encryption on the source server, send it to the destination server, and perform decryption on the destination server while logging the process to ensure a successful and secure delivery without any man-in-the-middle attacks.
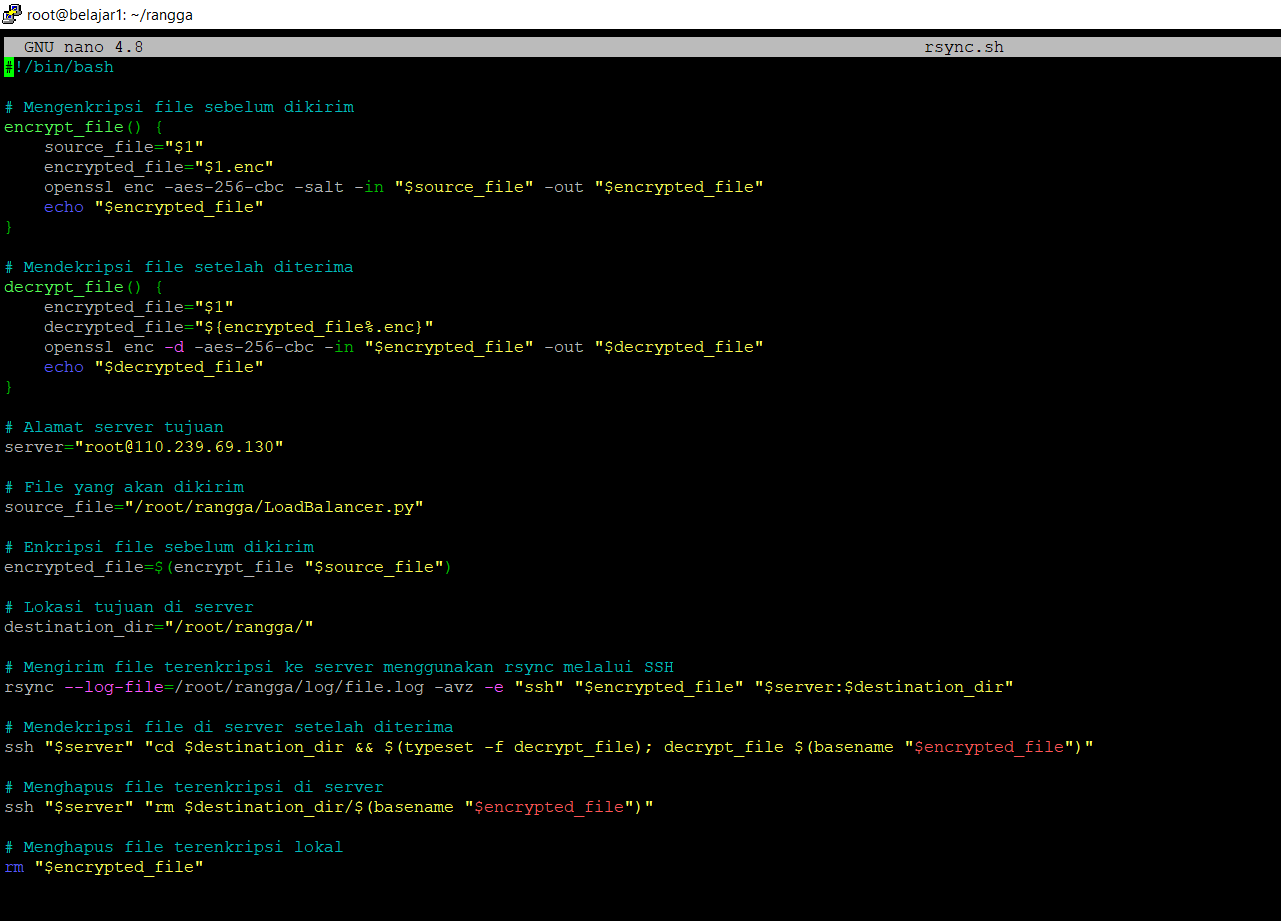
Create a bash script with the sh extension as follows: nano Rsync.sh
- Function encrypt_file(): This function takes one argument, which is the file path to be encrypted. It uses the openssl enc command to encrypt the file using the AES-256 algorithm in CBC (Cipher Block Chaining) mode with the addition of salt for increased security. The encrypted file will be saved with the .enc extension.
- Function decrypt_file(): This function takes one argument, which is the path to the encrypted file. It uses the openssl enc command with the -d option to decrypt the received encrypted file. The decrypted file will be saved with the same name as before encryption, without the .enc extension.
- Variable server: This variable contains the address of the destination server that will receive the sent file.
- Variable source_file: This variable contains the path to the file that will be sent to the server.
- File encryption: In this section, the file to be sent is encrypted using the encrypt_file() function, and the encryption result is stored in the variable encrypted_file.
- Variable destination_dir: This variable contains the destination location on the server where the file will be saved.
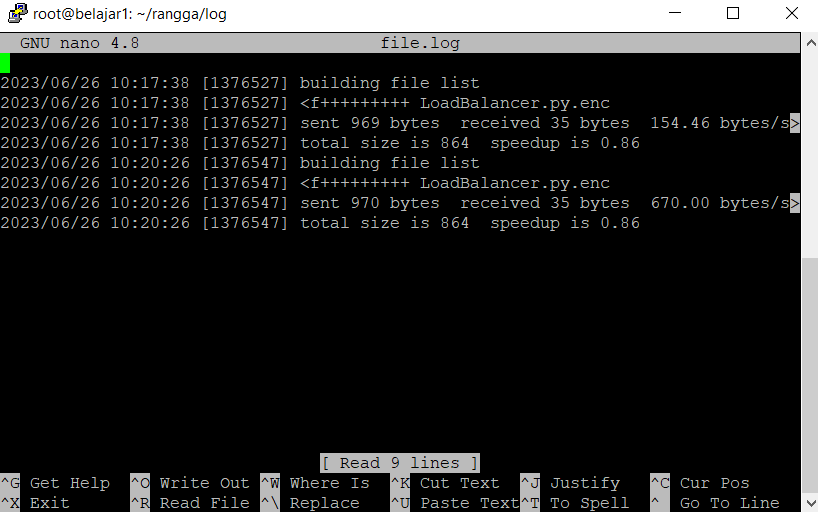
- File transmission: Using the rsync command, the encrypted file is sent to the destination server via SSH. Logs of the transmission process are saved in the file /root/rangga/log/file.log.
- File decryption on the server: After the file is sent, the script uses SSH to connect to the server and execute the decrypt_file() function on the server to decrypt the received file.
- Deletion of encrypted file on the server: After the file is decrypted on the server, the script uses SSH to delete the encrypted file on the server.
- Deletion of local encrypted file: After the transmission process is completed, the script deletes the local encrypted file on the sender's machine.
This script is used to secure the file transmission process by encrypting the file before sending it and decrypting the file after it is received on the server.
After creating and saving the script, give it executable permissions such as chmod +x Rsync.sh.
Then, execute the bash script with ./Rsync.sh.
Next, you will be asked for the encryption key or password, for example, 123, and perform key verification.
The next step will require the password for the destination server.
After entering the password for the destination server, you will see that the data has been successfully sent in the form of encrypted LoadBalancer.
After that, enter the password for the destination server and the AES encryption key to perform decryption.
It can also be seen that the LoadBalancer file has arrived at the destination server.
In the log, it can be seen that the process went smoothly and what was sent is the encrypted file, which is LoadBalance.py.enc.
Informasi Course Terkait
Kategori: Cyber SecurityCourse: Persiapan Sertifikasi Internasional CyberSAFE (Cyber Security Awareness For Everyone)